Write Us
We are just a call away
[ LET’S TALK AI ]
X
Discover AI-
Powered Solutions
Get ready to explore cutting-edge AI technologies that can transform your workflow!

Have you ever lost a potential enterprise deal because your SaaS platform didn’t meet their security requirements?
If yes, you are on the right page to ease your worry!
As more enterprises shift their operations to the cloud, their top concern isn’t just functionality, it’s security. They need assurance that the SaaS solutions they adopt can protect sensitive data. Also, meet compliance mandates and defend against ever-evolving cyber threats. If your product doesn’t deliver on these fronts, chances are it will be cut from their shortlist.
Integrating SaaS security best practices throughout the SaaS software development lifecycle is crucial to meet the rigorous expectations of enterprise clients. From architecture planning to deployment and ongoing updates, security must be embedded at every stage to prevent breaches and maintain customer trust.
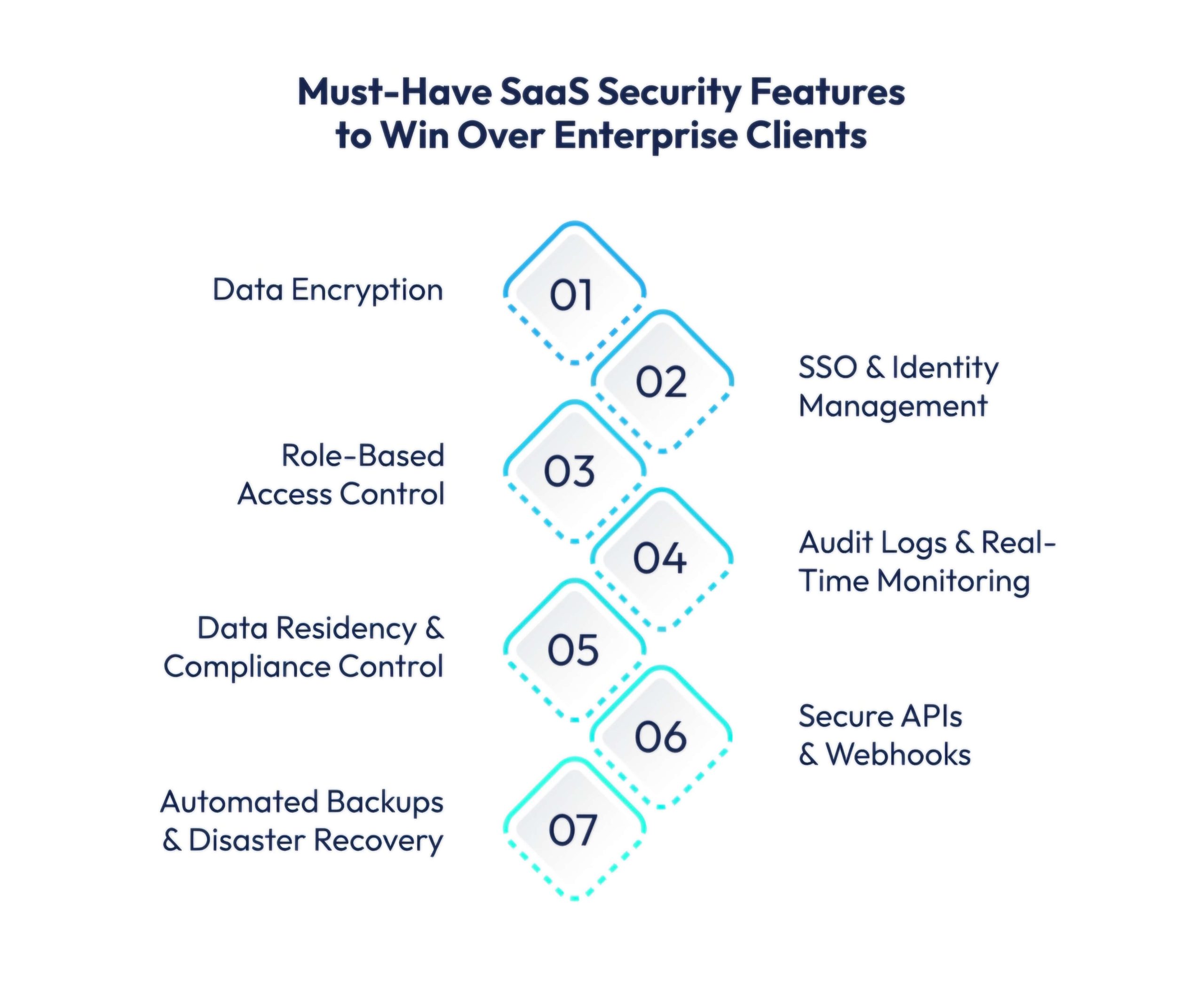
Aiming to land your first big client or a growing SaaS provider refining your security posture? These must-have features will strengthen your offering and help win over security-conscious enterprises.
We’ll be walking you through a comprehensive SaaS security checklist. Designed to help you build secure SaaS applications that align with enterprise SaaS security standards.
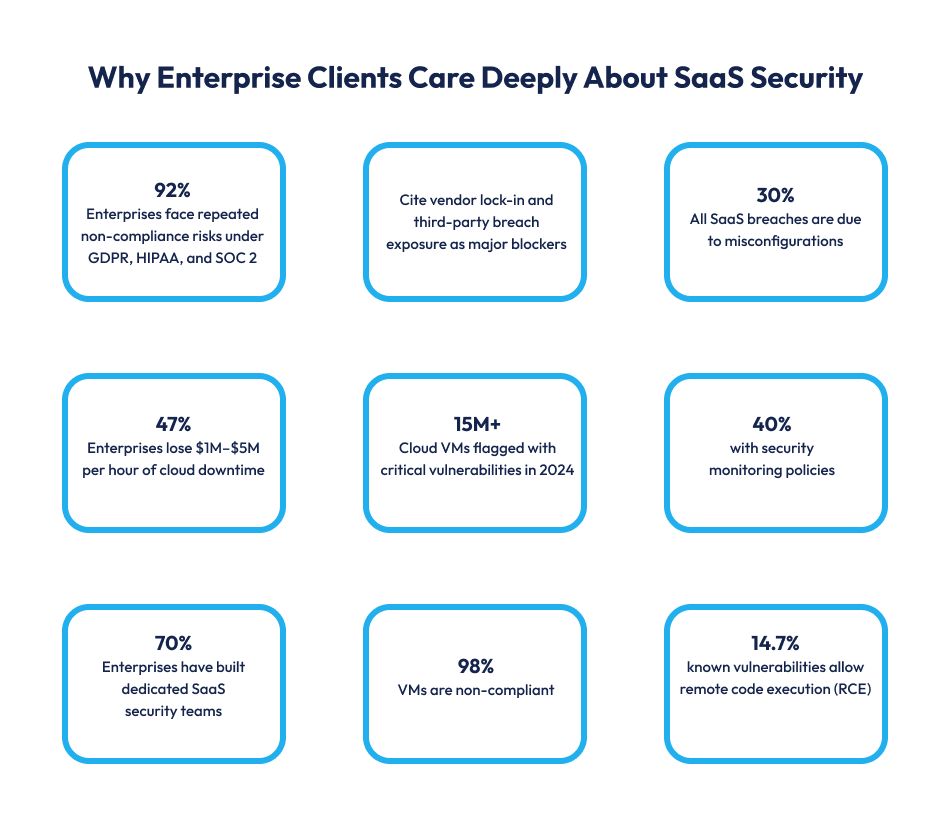
Enterprise clients demand robust enterprise SaaS security. Get engaged in why they care, often at a deeply personal and costly level.
Enterprises operate under regulations like GDPR, HIPAA, and SOC 2, where non-compliance can mean hefty fines and legal action. 92% of companies report repeated intrusion attempts within a year. This is due to the failure to safeguard sensitive data, which can lead to cascading liability. These regulatory burdens place compliance squarely at the heart of SaaS security best practices.
Vendor lock‑in is a major concern. 47% cite it as a top SaaS pain point. If one vendor misconfigures access or suffers a breach, entire enterprise stacks are at risk. A recent CISA alert flagged Commvault’s breach of client secrets, raising alarm on how deeply a third-party failure can impact downstream customers.
Complex SaaS environments lead to misconfigurations, the most common cause of breaches at 30%. One hour of downtime can cost enterprises over $100,000. With 40% reporting losses between $1–5 million per hour. Identity compromises drive 82% of SaaS breaches. MFA reduces unauthorized access risk by 99%. 70% of enterprises have created dedicated SaaS security teams, with budgets rising 39% and staff headcount up 56%. Demonstrating mature, secure SaaS application security credentials is a key differentiator for winning large deals.
Another mandate is real‑time threat visibility. Alarmingly, 98% of VMs fail to meet basic controls for monitoring changes within AWS environments. Leaving enterprises blind to malicious activity. Meanwhile, 14.7% of known vulnerabilities allow remote code execution (RCE), letting buyers assess exploitability risk before onboarding new SaaS.
On the flip side, investing in security pays off. Around 70% of enterprises have created dedicated SaaS security teams, with budgets rising by 39% and staffing up by 56%. Vendors showcasing a mature secure posture gain a clear competitive advantage and greater trust across enterprise buying cycles.
| Feature | Description | Enterprise Benefit | Real-World Example |
| Data Encryption (at Rest & in Transit) | – TLS 1.2+ for transit – AES-256 for stored data – Secure key management via KMS | – Blocks unauthorized access – Critical for finance, healthcare – Builds compliance readiness | – Zoom added AES-256 GCM – Helped recover trust post-privacy backlash |
| SSO & Identity Management (OAuth 2.0, SAML, SCIM) | – Connects to Okta, Azure AD – Enables SSO and MFA – Syncs user roles via SCIM | – Streamlines user access – Reduces shadow IT – Speeds up onboarding/offboarding | – Slack scaled enterprise growth – Rolled out SSO, SCIM, granular role access |
| Role-Based Access Control (RBAC) | – Defines access by roles – Fine-grained permissions – Contextual conditions (e.g. IP, time) | – Limits privilege escalation – Prevents insider misuse – Aligns with least privilege model | – Notion lets teams set view/edit rights – Enables document-level security |
| Audit Logs & Real-Time Monitoring | – Tracks user actions, API calls – Alerts on anomalies – Integrates with SIEM tools | – Helps with audit trails – Enables incident forensics – Supports SOC 2, HIPAA | – Salesforce Shield offers field-level logs – Sends real-time alerts for unusual behavior |
| Data Residency & Compliance Control | – Let users select region – Supports GDPR, CCPA, etc. – Multi-region infrastructure | – Meets legal obligations – Supports regional governance – Appeals to regulated sectors | – Azure enables country-specific hosting – Popular in finance and healthcare |
| Secure APIs & Webhooks | – Uses OAuth tokens – Applies rate-limits & schema checks – Enforces webhook signing | – Prevents API abuse & injection – Secures third-party integrations | – Stripe uses versioned APIs – Requires webhook signatures to block tampering |
| Automated Backups & Disaster Recovery | – Daily encrypted backups – Point-in-time restore (PITR) – Geo-redundancy for failover | – Prevents data loss – Ensures availability (SLA-grade) – Defends against ransomware | – Dropbox Enterprise offers auto-backups – Restores critical files with minimal downtime |
To meet compliance mandates and avoid breaches, SaaS providers must embed security throughout both SaaS architecture and the software development lifecycle (SDLC).
Here’s how to do it effectively:
Your SaaS architecture is the foundation of your application, and it needs to be secure by design. This means:
By integrating security into your CI/CD pipeline, you reduce risk before release. This shift-left approach ensures security flaws are caught while they’re cheapest to fix.
Most SaaS breaches stem from poor access controls. These measures enforce least-privilege access and reduce the blast radius of insider threats:
APIs are the lifeblood of SaaS, but they’re also the most exploited.
Security at the infrastructure level reduces exposure and protects the app from lateral movement during attacks. Beyond the app layer, your infrastructure must be locked down.
Detection is as critical as prevention. Being proactive here boosts your enterprise readiness posture. Integrate tools to monitor and respond:
Enterprises expect their data to be secure and recoverable at all times. This builds resilience and earns client trust through transparency and preparedness.
Even the most secure architecture fails without human alignment. Encourage:
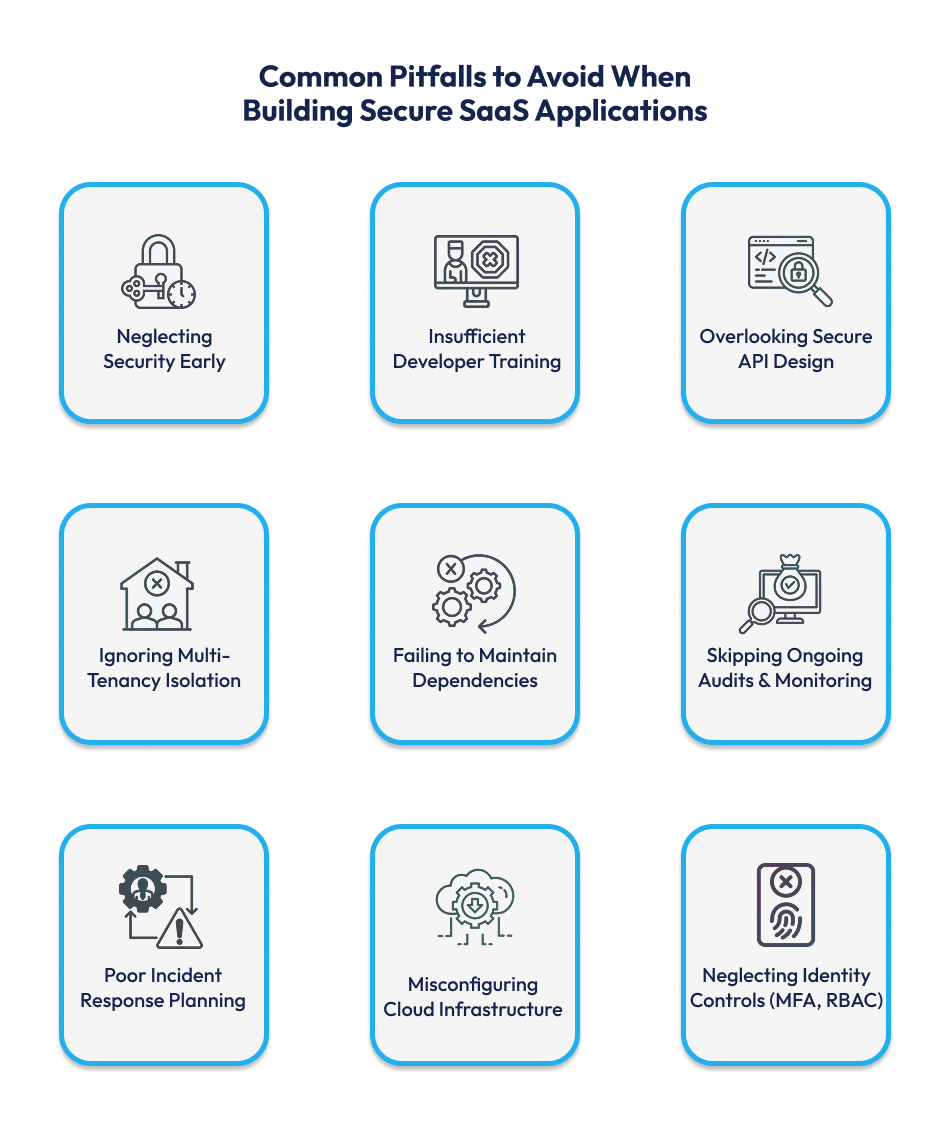
For a SaaS contract management solution, understanding the common mistakes in secure SaaS application development services can save time, budget, and customer trust. Avoiding these traps mitigates risk and strengthens your value proposition:
| Pitfall | Why It Matters in SaaS | How to Avoid It | Key Benefit |
| Neglecting Security Early | Delaying security integration leads to expensive retrofits, compliance gaps, and vulnerabilities | Embed threat modeling, secure design, and DevSecOps from the MVP stage | Lowers risk and cost; builds stronger SaaS architecture |
| Insufficient Developer Training | Lack of secure coding knowledge introduces OWASP-level issues into SaaS workflows | Provide ongoing secure coding education and appoint security champions | Fosters a secure dev culture and reduces bugs |
| Overlooking Secure API Design | Insecure APIs/webhooks are high-risk vectors in contract management tools | Enforce token auth, rate limits, schemas, signed webhooks, and frequent testing | Prevents data leaks and integration abuse |
| Ignoring Multi-Tenancy Isolation | Poor isolation in contract data stores can lead to cross-customer leaks | Implement strict tenant boundaries, segmented data stores, and access controls | Ensures data confidentiality and compliance in shared environments |
| Failing to Maintain Dependencies | Outdated libraries expose contract systems to known attacks | Use automated dependency scanners and CI/CD pipelines for patching | Keeps SaaS secure and compliant with minimal effort |
| Skipping Ongoing Audits & Monitoring | Relying on initial security without continuous monitoring risks hidden breaches | Schedule regular penetration tests, audits, and real-time logging | Detects threats early, supports forensic investigations |
| Poor Incident Response Planning | No defined breach plan causes delays and damages trust in contracts | Create and rehearse a response plan: detect, contain, recover, improve | Accelerates recovery and maintains client confidence |
| Misconfiguring Cloud Infrastructure | Misunderstanding shared responsibility leads to oversights in cloud setups | Use CSPM tools, infra-as-code, regular config reviews | Prevents misconfigurations and audit failures |
| Neglecting Identity Controls (MFA, RBAC) | Weak access control is a major entry point for contract data breaches | Require MFA, enforce RBAC, and conduct permission audits | Protects sensitive workflows and reduces insider risk |
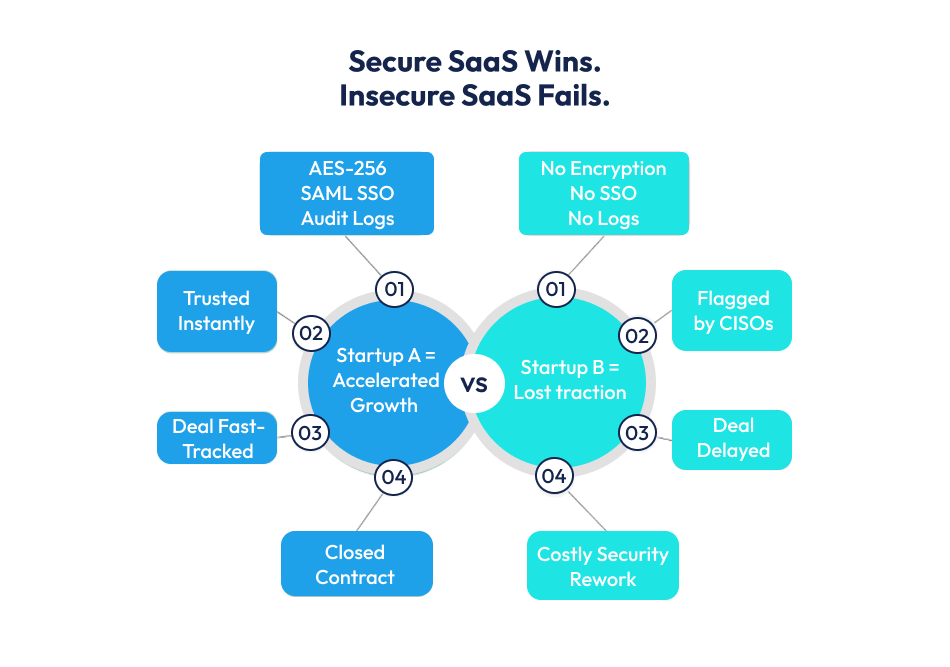
When it comes to B2B SaaS MVP development, the line between triumph and disaster can be as thin as a secure encryption key.
A startup launches a contract management SaaS MVP without security features, including encryption, SSO, or audit logs. As they pitch to an enterprise, CISOs flag vulnerabilities in a quick review. The deal stalls. Weeks spent courting the client are lost, pivoting to retrofit security costs months and thousands in rework.
The outcome? Fail.
A competing MVP is built with DevSecOps, embedded SAML-based SSO, AES-256 encryption, tenant isolation, and audit logging from day one. During demos, the startup highlights these features, CISOs immediately see reduced risk, procurement fast-tracks, and the contract closes.
The outcome? Win.
That early investment in security transforms it from a perceived cost to a deal catalyst. Amplifying SaaS marketing success and accelerating traction in enterprise pipelines.
AI-powered custom SaaS solutions often handle sensitive workflows, from predictive analytics to automated contract review. Buyers evaluate not just model quality but also data governance, API security, and run-time monitoring. Vendors who demonstrate AI-driven security features, like automated anomaly detection or predictive threat blocking. Additionally, they also showcase continuous monitoring and adaptive controls to gain enterprise confidence. AI-based security tools (e.g., Reco) have recently raised $55M, underscoring buyer demand for secure AI-first SaaS
A shift in buyer preferences is underway. According to B2BDaily, enterprises now view security as a core differentiator in SaaS selection, especially given the average cost of $4.45M for data breaches. Vendors who lead with security in their marketing often outperform competitors:
| Tactic | Why It Matters | Example |
| Security-focused onboarding | Position security as a value-add from day one | Our MVP includes SSO, encryption, and PCI logging |
| Marketing collateral | Builds trust with details on encryption, compliance, and auditability | Feature sheets, case studies, and datasheets |
| Live demos of security controls | Impresses technical buyers by demonstrating team readiness | Show real-time logs, RBAC, and response workflows |
| Certifications & 3rd-party audits | Validates claims and eases internal procurement risk | SOC 2, ISO 27001, penetration-test reports |
| AI in security messaging | Appeals to tech-savvy buyers in AI SaaS | Our engine flags anomalies in seconds using AI |
For B2B SaaS MVPs and AI-driven platforms, early security builds credibility, accelerates enterprise adoption, and unlocks growth. Leading with this in your SaaS marketing narrative helps you stand out, transforming security from a risk at the finish line into a competitive advantage from the first line of code. To get it right from the start, partner with the best AI app development company that embeds security and compliance into every layer of your product.
Key Strategies for Enhancing Cybersecurity SaaS Security & a Resilient Digital Infrastructure
Building secure SaaS applications is about trust, growth, and long-term enterprise success. From encryption and access controls to audit trails and secure DevOps, every layer of your SaaS architecture must reflect maturity and readiness.
So what did you learn today?
Invest in secure SaaS applications with the help of trusted experts. Partner with Techugo, a leading provider of end-to-end SaaS enterprise application development services.
Who’s Techugo?
Techugo is a global enterprise AI development company delivering scalable, secure, and enterprise-grade SaaS software development services. Whether you’re launching a B2B MVP or scaling an AI-powered platform, Techugo brings deep expertise in SaaS architecture. And expert compliance readiness, and cloud-native security. Our experts are your go-to partner for fast-growing startups and global enterprises alike.
Let’s build something secure, together with one of the best AI saas companies.
Write Us
sales@techugo.comOr fill this form